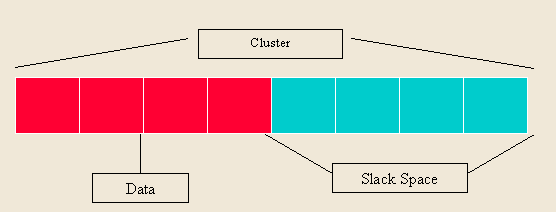
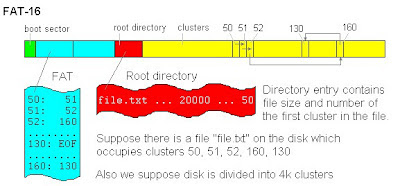
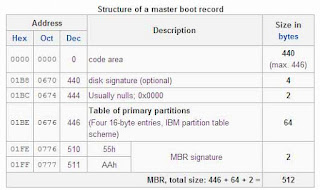
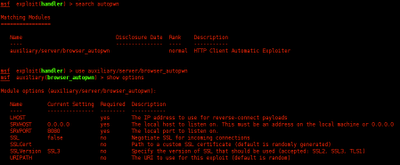
Digital Forensic: Analysis

The next article , I 'll try to give a little tutorial how to analyze . certainly still part of the digital forensic . Download the file here The first step is the analysis organization Analysis organization root@bt:~# dd if=practical.floppy.dd of=/dev/fd0 then output is create a folder