Beef and Metasploit (2)
i will try to explore more deeply about the beef and metasploit
entered the scenario
open beef and send an alert
here I ordered the victim to perform updates microsoft office 2012
we forced the victim to download a program and run it
Do not forget we are listening to multi handler
what happened?
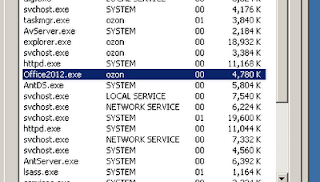
the victim was truly obey our commands
now you already know what the actual contents of office2012.exe :)
I did generate a payload and save it with name office2012.exe,
if carelessness like this still happened, we did not rule out a system skipper :)
entered the scenario
open beef and send an alert
here I ordered the victim to perform updates microsoft office 2012
we forced the victim to download a program and run it
Do not forget we are listening to multi handler
what happened?
the victim was truly obey our commands
now you already know what the actual contents of office2012.exe :)
I did generate a payload and save it with name office2012.exe,
if carelessness like this still happened, we did not rule out a system skipper :)






Comments
Post a Comment