Privilege Escalation (2)
In my previous post I promised to discuss how to cracking passwords with john the ripper. before entering the phase of cracking, I will introduce what it is john the ripper.
John the Ripper is a fast password cracker. There are some important things to JTR
[Passfile] - The name of the password file you
[Wordlist] - Collection of the words
[Output] - Results decrypt passwords
- Password File example: password.txt -
vmware: $ 1 $ 7nwi9F / D $ AkdCcO2UfsCOM0IC8BYBb /: 14042:0:99999:7:::
Obama: $ 1 $ hvDHcCfx $ pj78hUduionhij9q9JrtA0: 14041:0:99999:7:::
osama: $ 1 $ Kqiv9qBp $ eJg2uGCrOHoXGq0h5ehwe.: 14041:0:99999:7:::
yomama: $ 1 $ tI4FJ.kP $ wgDmweY9SAzJZYqW76oDA.: 14041:0:99999:7:::
There are 3 modes in the JTR to decrypt the password
1. Single Mode
In Single Mode, JTR will try to find password quickly.
command:
john-the passwd.txt
2. Wordfile Mode
command:
john-w: words.lst password.txt
3. Incremental Mode
command
john-i passwd.txt
john-i: digits passwd.txt
john-i: ALPHA passwd.txt
john-i: ALL passwd.txt
to see the results we type the command
command:
john-show password.txt> hasil.txt
You can also see directly from JTR decrypt the results by typing the command
john-show [passfile]
All passwords are never stored in the crack in john.pot JTR
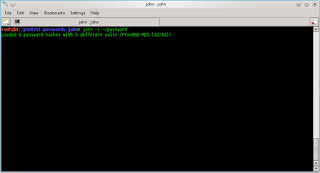
Immediately, in the discussion, the previous post we have been copying etc / shadow into a txt file with the name of the password. we will try cracking with thhe john ripper, simply go to JTRtype the command
john-i ~ / passwd.txt
wait until the process is complete:)
John the Ripper is a fast password cracker. There are some important things to JTR
[Passfile] - The name of the password file you
[Wordlist] - Collection of the words
[Output] - Results decrypt passwords
- Password File example: password.txt -
vmware: $ 1 $ 7nwi9F / D $ AkdCcO2UfsCOM0IC8BYBb /: 14042:0:99999:7:::
Obama: $ 1 $ hvDHcCfx $ pj78hUduionhij9q9JrtA0: 14041:0:99999:7:::
osama: $ 1 $ Kqiv9qBp $ eJg2uGCrOHoXGq0h5ehwe.: 14041:0:99999:7:::
yomama: $ 1 $ tI4FJ.kP $ wgDmweY9SAzJZYqW76oDA.: 14041:0:99999:7:::
There are 3 modes in the JTR to decrypt the password
1. Single Mode
In Single Mode, JTR will try to find password quickly.
command:
john-the passwd.txt
2. Wordfile Mode
This is the fastest way to second but the JTR requires dictionary words
john-w: words.lst password.txt
3. Incremental Mode
In this way the slowest because it takes many days to download decrypt all passwords
john-i passwd.txt
john-i: digits passwd.txt
john-i: ALPHA passwd.txt
john-i: ALL passwd.txt
to see the results we type the command
command:
john-show password.txt> hasil.txt
You can also see directly from JTR decrypt the results by typing the command
john-show [passfile]
All passwords are never stored in the crack in john.pot JTR
Immediately, in the discussion, the previous post we have been copying etc / shadow into a txt file with the name of the password. we will try cracking with thhe john ripper, simply go to JTRtype the command
john-i ~ / passwd.txt
wait until the process is complete:)


Comments
Post a Comment