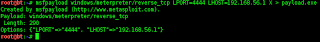
Msfpayload is one of the tools included with the Metasploit Framework . It can be used to the make the payload . Adjusted for the period , first select one of the many charges Including the core framework. Then give the parameters for the charge and the output format you want, so it can be said of this tool is to generate a custom payload we want . You can take the file generated in the exploitation of its own and is written in C , Ruby , Perl , Java or other languages . msfpayload also has the ability to create executable programs . It is used by who Attackers want to get full access to the target machine . It is also useful for who attackers want to use the charge Meterpreter , IDS and forensic examples of the use of: