BigAnt Server
I'll see you again :)The next is to learn about the exploitation of SEH, which I practice today is to use a direct returnjust to try it.this is a big application server that will be our ant exploitation,OllyDbg is open on the application, and attachkan prosess antServer, our next step is to make the application to crash, with a script / fuzzer follows.
different from the last application, the EIP register are not affected by the fuzzer is sent, to know the SEH, we go to the menu view> SEH chain
turns out that we send buffer is stored there, to continue press SHIFT + F9if successful, then the value of EIP will be crushed.
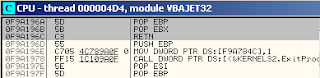
And to see the data buffer in memory, we can right click on the stack select follow in dump.there will be seen the data that we sent earlier.The next step is to find a stepping stone here I use vbajet32.dllwe find the location of the command POP, POP RETN by clicking view> Executable Modules> select vbajet32.dll
do a search with a sequence of commands
if successful then we will be redirected to an address.
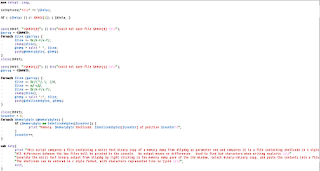
step after that is to make the pattern I need not explain how to create a pattern, we create a pattern of 2500 bytes. And do the income into the fuzzer.
Do not forget, we run each application, we repeat steps as in the initial attach.after our fuzzer script SEH bay pass, as the first step, ie press F9note the value of the EIP register and do check with offset pattern.
after we know the value of the EIP registerthen we do enter into the fuzzer script as shown below
if successful then the value of EIP will be changed to \ X41
before running the fuzzer, create a breakpoint on memory address 0F9A196AThe process will be visible when accessing the address, to see, try entering the table SEH chain.press shift + F9 to continue the process.
to see memory, right click on the first address> follow in dump> selection
what happens, when we try to enter the SEH chain, where the data show 90909090
after we test by eliminating the payload, it turns out in the SEH chain pointing to the correct address,
as the case of the other cases, these problems usually occur due tobad character, to look for bad characters we must look for the manual, before we use the script generates the following codes
The next is to enter one by one line of generated codes before, do as the steps below.
and it turns out the first line is still pointing to the correct address,
the next is entering the second row,
do testing with dummies shellcode, and then see if it is to the right address.
it turns out bad character is \ x25,
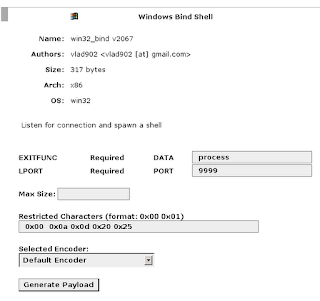
the next step is to make the payload by adding bad character \ x20 and \ x25
paylaod enter into the fuzzer
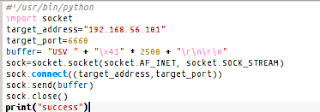
and try connecting
Yes, we managed to exploit the BigAnt Server.
different from the last application, the EIP register are not affected by the fuzzer is sent, to know the SEH, we go to the menu view> SEH chain
turns out that we send buffer is stored there, to continue press SHIFT + F9if successful, then the value of EIP will be crushed.
And to see the data buffer in memory, we can right click on the stack select follow in dump.there will be seen the data that we sent earlier.The next step is to find a stepping stone here I use vbajet32.dllwe find the location of the command POP, POP RETN by clicking view> Executable Modules> select vbajet32.dll
do a search with a sequence of commands
if successful then we will be redirected to an address.
step after that is to make the pattern I need not explain how to create a pattern, we create a pattern of 2500 bytes. And do the income into the fuzzer.
Do not forget, we run each application, we repeat steps as in the initial attach.after our fuzzer script SEH bay pass, as the first step, ie press F9note the value of the EIP register and do check with offset pattern.
after we know the value of the EIP registerthen we do enter into the fuzzer script as shown below
if successful then the value of EIP will be changed to \ X41
then we enter into the SEH address fuzzer script did like the script below
to see memory, right click on the first address> follow in dump> selection
The next is to make the payload, as usual, I use the metasploit web, you can use another.do as the steps below.
insert the payload into the fuzzer script, this script is added with the NOP and JMP SHORT
after we test by eliminating the payload, it turns out in the SEH chain pointing to the correct address,
as the case of the other cases, these problems usually occur due tobad character, to look for bad characters we must look for the manual, before we use the script generates the following codes
The next is to enter one by one line of generated codes before, do as the steps below.
and it turns out the first line is still pointing to the correct address,
the next is entering the second row,
there was SEH chain leads to 90909090, to conduct a search, to generate these codes into 2 for easy,
do to make the character \ x20 as a bad character
do to make the character \ x20 as a bad character
do generate more use generatecodes by adding 20 as a bad character.
do testing with dummies shellcode, and then see if it is to the right address.
then again in anticipation of bad character, we do check bad character in the buffer by
The first is for the first breakpoint at address 0F9A196A then run the application and do fuzzing
then press shift + F9 and press f7 to pass command POP, POP RETN, after leading to JMP SHORT, press F7
The next step is reading the buffer is in memory by means of existing dump memory contents by right-clicking Follow in dump> selection
select data from 01 to FF, then copy the binary tersebut.paste binary data that we copied earlier into the text editor save the name memory.txt
do the same storage by 00.0 generatecodes with a bad character, 0d, 20 save with the name shellcode.txt
use the script below to compare
there appear differences in the opcode, to check, enter the code one by one into generatecodes and do a test with a fuzzer.The first is for the first breakpoint at address 0F9A196A then run the application and do fuzzing
then press shift + F9 and press f7 to pass command POP, POP RETN, after leading to JMP SHORT, press F7
The next step is reading the buffer is in memory by means of existing dump memory contents by right-clicking Follow in dump> selection
select data from 01 to FF, then copy the binary tersebut.paste binary data that we copied earlier into the text editor save the name memory.txt
do the same storage by 00.0 generatecodes with a bad character, 0d, 20 save with the name shellcode.txt
use the script below to compare
it turns out bad character is \ x25,
the next step is to make the payload by adding bad character \ x20 and \ x25
paylaod enter into the fuzzer
and try connecting
Yes, we managed to exploit the BigAnt Server.



























Comments
Post a Comment