Mini Stream RM-MP3 converter
yess, this time I will demonstrate how to exploit rm-mp3 converterjust in the discussion. The first thing we do is find an exploit on exploit-db,

poorer exploit we find, then we select the local stack overflow then we edit the perl script.done as follows.
to the way we use load via rm-mp3 converter, it is up how do we generate a file that was up to the virtual windows, with var / www or through anyafter load poorer rm-mp3 converter disappear from the screen, to find out what happened, we find out through Olly tools.turns out that we created earlier fiile legible on memory EIP.
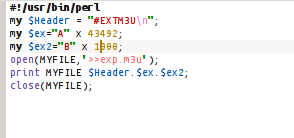
as well as exploit the WAR, we use the pattern to create the data to make regular, lighter read that data, we ex broke into 2 parts.we just try to create 1000 data.
then after the 1000 data we put in the script,
the value of the FPU register changes its value,
it is the value that we will find the tools offset pattern
after we find the next step is to find the value DEDEBABEwrite the script as below.
to execute the same as the first step, we load the file. m3u to the application.
next step is to overwrite the ESP with the NOP. The following script code.
if successful, then the value will change in the lower right corner to 90909090It signifies our success ESP override, your smile.
The next step is to find a stepping stone that is JMP ESP, at this time I use shell32.dll, please explore :)
after we found out, note the address of JMP ESP, make a change in DEDEBABE, do not forget the little indian format.
and the last step is the code generate payload, metasploit I use the web, do as shown below ..
after all be included in the perl script, we immediately load the rm-mp3 converter. what happened?hang, do not worry, it indicates if we are successful, do the test by telnet or nc to the target computer.
good luck, do not easily discouraged

poorer exploit we find, then we select the local stack overflow then we edit the perl script.done as follows.
to the way we use load via rm-mp3 converter, it is up how do we generate a file that was up to the virtual windows, with var / www or through anyafter load poorer rm-mp3 converter disappear from the screen, to find out what happened, we find out through Olly tools.turns out that we created earlier fiile legible on memory EIP.
as well as exploit the WAR, we use the pattern to create the data to make regular, lighter read that data, we ex broke into 2 parts.we just try to create 1000 data.
then after the 1000 data we put in the script,
the value of the FPU register changes its value,
it is the value that we will find the tools offset pattern
after we find the next step is to find the value DEDEBABEwrite the script as below.
to execute the same as the first step, we load the file. m3u to the application.
next step is to overwrite the ESP with the NOP. The following script code.
if successful, then the value will change in the lower right corner to 90909090It signifies our success ESP override, your smile.
The next step is to find a stepping stone that is JMP ESP, at this time I use shell32.dll, please explore :)
after we found out, note the address of JMP ESP, make a change in DEDEBABE, do not forget the little indian format.
and the last step is the code generate payload, metasploit I use the web, do as shown below ..
after all be included in the perl script, we immediately load the rm-mp3 converter. what happened?hang, do not worry, it indicates if we are successful, do the test by telnet or nc to the target computer.
good luck, do not easily discouraged

















Comments
Post a Comment