Social Engineering and SET
What Exactly Is Social Engineering?
Actual social engineering technique is not nothing but a deceptive techniques is another human being. The goal is to get something he wanted. Not only in the form of money or property only, but many of Things Such as information, power, victory, and more. Social engineering activity in the IT world can not be separated from human manipulation interact the computer by using a combination of Various techniques Such as spy, steal, lie, distort facts, and more. Attackers using social engineering usually do not need a set of advanced tools or software can solve difficult, That codes. Required in the process is the understanding of this attack is psychological condition of the target, and of course also Eloquence.
Who is the Target Social Engineering?
none other than the people WHO have something of value required by the attacker would have been the main target. In the world of IT people WHO have Important information, both in the head and on his computer is the main target of social engineering. The goal is to gather Important Such information but rather from his computer, but directly from users.Do what is usually the attacker?Important Gather information from others can be anything. For example to get information login and password to enter into the company intranet, tricking users to open e-mail containing a backdoor for later visited by the hackers, stealing data like eg konvidensial marketing strategy, new products, and more. This data would be very valuable sekalibagi WHO people need them later.
How Can Someone Make Social Engineering?
who data security criminals conduct social engineering is usually good at understanding human nature and habit. In Addition, the ability to persuade others to Provider information is the capital of the hackers of this type. Persuade yourself or persuasion is actually almost be categorized as an art and then combined with the abilitytechnology in this case social engineering. One study showed That most Humans have some traits in growing niche to be exploited That easily by using a specific manipulation techniques. Finally, by Applying this technique in Humans, the positive response will be obtained from it. And that is unfortunate Among many men are endowed with WHO you the ability and talent to Manipulate naturally, and not least also a study for the purpose of Positively and negatively.
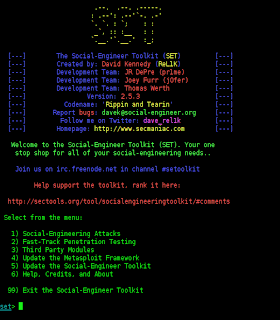
Social-Engineering Toolkit (SET)
Social-Engineering Toolkit (SET) is specifically designed to carry out further attacks against the human element. SET has rapidly become a standard tool in the arsenal of penetration testers. SET was written by David Kennedy (ReL1K) and with much help from the community in combining attacks never before seen in a toolset exploitation. The attack, the which is built into the toolkit is designed to target a focused attack against a person or organization used during the penetration test.
Actual social engineering technique is not nothing but a deceptive techniques is another human being. The goal is to get something he wanted. Not only in the form of money or property only, but many of Things Such as information, power, victory, and more. Social engineering activity in the IT world can not be separated from human manipulation interact the computer by using a combination of Various techniques Such as spy, steal, lie, distort facts, and more. Attackers using social engineering usually do not need a set of advanced tools or software can solve difficult, That codes. Required in the process is the understanding of this attack is psychological condition of the target, and of course also Eloquence.
Who is the Target Social Engineering?
none other than the people WHO have something of value required by the attacker would have been the main target. In the world of IT people WHO have Important information, both in the head and on his computer is the main target of social engineering. The goal is to gather Important Such information but rather from his computer, but directly from users.Do what is usually the attacker?Important Gather information from others can be anything. For example to get information login and password to enter into the company intranet, tricking users to open e-mail containing a backdoor for later visited by the hackers, stealing data like eg konvidensial marketing strategy, new products, and more. This data would be very valuable sekalibagi WHO people need them later.
How Can Someone Make Social Engineering?
who data security criminals conduct social engineering is usually good at understanding human nature and habit. In Addition, the ability to persuade others to Provider information is the capital of the hackers of this type. Persuade yourself or persuasion is actually almost be categorized as an art and then combined with the abilitytechnology in this case social engineering. One study showed That most Humans have some traits in growing niche to be exploited That easily by using a specific manipulation techniques. Finally, by Applying this technique in Humans, the positive response will be obtained from it. And that is unfortunate Among many men are endowed with WHO you the ability and talent to Manipulate naturally, and not least also a study for the purpose of Positively and negatively.
Social-Engineering Toolkit (SET)
Social-Engineering Toolkit (SET) is specifically designed to carry out further attacks against the human element. SET has rapidly become a standard tool in the arsenal of penetration testers. SET was written by David Kennedy (ReL1K) and with much help from the community in combining attacks never before seen in a toolset exploitation. The attack, the which is built into the toolkit is designed to target a focused attack against a person or organization used during the penetration test.


Comments
Post a Comment